Stuxnet Code: The Virus that Almost Started WW3
Autorius: Rory John Gates Šaltinis: https://voicemed.webflow.io/lt... 2020-12-10 21:33:00, skaitė 2716, komentavo 2
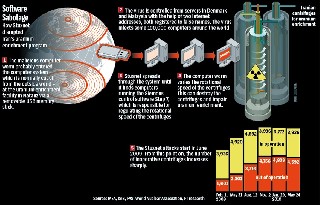
Stuxnet is not only a new virus or worm but it's a new era of malware. This virus changed the meaning of malware and their goals. You hear about a virus annoying people or stealing banks or credit cards, but that's the first time you hear about virus damages buildings, destroys machines or kills people and that's Stuxnet. Stuxnet has gained a lot of attention from malware researchers and media in the last year. It's created to sabotage Iran's nuclear program. This complex threat uses up to four zero-day vulnerabilities in windows OS and includes many tricks to avoid being detected by the behavioral-blocking antivirus programs. It damaged the Iranian nuclear reactor and its machines by infecting the PLCs (Programmable Logic Controller) that control the machines there. That makes it modify the control program which changes the behavior of the machine.
Here we will talk about the technical details about stuxnet and the experience that I got from analyzing this malware. We will talk about how stuxnet works and the stuxnet life cycle. But here we will not talk about the SCADA systems and how stuxnet infects them and we will take a hint on the vulnerabilities that are used by stuxnet.This worm was created mainly to sabotage the Iranian Nuclear Program. Once installed on a PC, Stuxnet uses Siemens' default passwords to gain access to the systems that run the WinCC and PCS 7 programs which control and modify the code of the PLCs (programmable logic controller) which control the machines themselves Stuxnet operates in two stages after infection, according to Symantec Security Response Supervisor Liam O'Murchu. First it uploads configuration information about the Siemens system to a command-and-control server. Then the attackers are able to pick a target and actually reprogram the way it works. "They decide how they want the PLCs to work for them, and then they send code to the infected machines that will change how the PLCs work," O'Murchu said. It managed to infect facilities tied to Iran's controversial nuclear programme before re-programming control systems to spin up high-speed centrifuges and slow them down
1. Introduction:Stuxnet
2. Stuxnet Worm Source Code
3. Decompilation of Stuxnet.
Rory John Gates human killer